Publisher's description
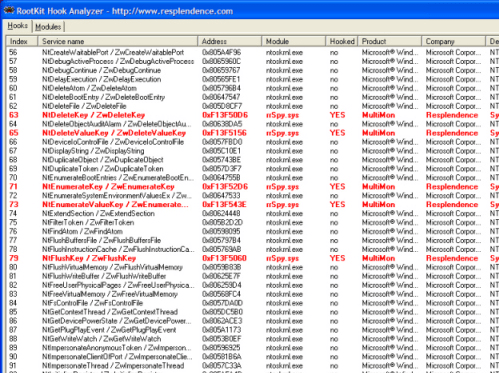
RootKit Hook Analyzer is a security tool which will check if there are any rootkits installed on your computer which hook the kernel system services. Kernel RootKit Hooks are installed modules which intercept the principal system services that all programs and the operating system rely on.
If any of these system services are intercepted and modified it means that there is a possibility that the safety of your system is at risk and that spyware, a virus or other malware is active on your system. Kernel hooks are not necessarily bad, for system monitoring software and security tools often they are a necessary evil. However it is desired if kernel rootkit hooks are installed on your system that you can find out where they come from. This program will display all kernel services and the responsible modules for handling them, along with company and product information. If no hooks are active on your system it means that all system services are handled by NTOSKRNL.EXE, the principal base component of most Windows operating systems which is developed by Microsoft. All you have to do to find out what kernel hooks are installed on your system is press the Analyze button at the bottom of the screen. RootKit Hook Analyzer also allows you to view installed system modules and drivers with their base addresses as well as file and product information as well as the responsible companies.
New is the option to tets the quality of system hooks. If you have legitimate software installed which uses system call hooks, you can test if they are properly implemented by using the hook test function. This way you can see if hooking third-party system software may be responsible for random reboots and blue screens on your system.
The software is distributed as a free download. For more information visit http://www.resplendence.com/hookanalyzer
If any of these system services are intercepted and modified it means that there is a possibility that the safety of your system is at risk and that spyware, a virus or other malware is active on your system. Kernel hooks are not necessarily bad, for system monitoring software and security tools often they are a necessary evil. However it is desired if kernel rootkit hooks are installed on your system that you can find out where they come from. This program will display all kernel services and the responsible modules for handling them, along with company and product information. If no hooks are active on your system it means that all system services are handled by NTOSKRNL.EXE, the principal base component of most Windows operating systems which is developed by Microsoft. All you have to do to find out what kernel hooks are installed on your system is press the Analyze button at the bottom of the screen. RootKit Hook Analyzer also allows you to view installed system modules and drivers with their base addresses as well as file and product information as well as the responsible companies.
New is the option to tets the quality of system hooks. If you have legitimate software installed which uses system call hooks, you can test if they are properly implemented by using the hook test function. This way you can see if hooking third-party system software may be responsible for random reboots and blue screens on your system.
The software is distributed as a free download. For more information visit http://www.resplendence.com/hookanalyzer


User comments